Thursday, April 19, 2012
Tag :// Facebook
Monday, April 16, 2012
Memory Cards are the external storage media that are used to store digital information. Most of the users store music, videos and photos in the memory cards. But some experienced users also stores confidential information, contacts, messages etc in it and sets up the password to protect it from unauthorized access. However if you forget your password then recovering your data can be a nightmare for most users. Even mobile companies don’t provide any software to remove password protection. If you connect the password protected memory card with your computer using USB then it will not show any extra hard drive in your Windows Explorer. The only solution left is to Format the memory card from your mobile phones.
FExplorer is freeware third party small utility which will bring sigh of relief to users who forgot their memory card password. FExplorer only works with Nokia s60 first and second Edition phones.
First of all, Download FExplorer in to your mobile phone.
Now run FExplorer and go to C: drive first.
Now get into C:\System folder.
Search for the mmcstore file name and copy this file into your computer.
Now open this file with Notepad in your computer.
Now you will be able to see the memory card password in this notepad file.
Tag :// cool Tricks
Sunday, April 15, 2012
Hello friends,How are you?
In this post I am explaining about some concept of cookies and how to retrive or delete them with the help of some software tools.
So,Basically What is a Cookie?
A cookie, also known as an HTTP cookie, web cookie, or browser cookie, is used for an origin website to send state information to a user's browser and for the browser to return the state information to the origin site.
The state information can be used for authentication, identification of a user session, user's preferences, shopping cart contents, or anything else that can be accomplished through storing text data.
Cookies are not software. They cannot be programmed, cannot carry viruses, and cannot install malware on the host computer .However, they can be used by spyware to track user's browsing activities – a major privacy concern that prompted European and US law makers to take action. Cookies could also be stolen by hackers to gain access to a victim's web account.
>>>>>>Here I am using Software named CookieView to retrieve
cookies>>>>>>
Now,When you will run the software first time,you will see previously stored cookies in your computer as shown <remember this is my computer cookies>:
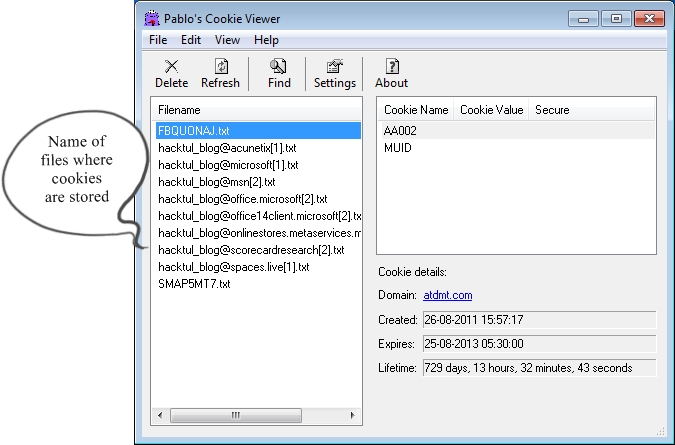
1 The Filename which is highlighted i.e FBQUONAJ.txt has following information as given below:
Cookie Details:
Domain: Last Visited Domain.
Created: Date of visit that domain.
Expires: Date of automatic deletion in future.
Lifetime: Time left.
As this is my computer browser cookie.Changes may takes place from computer to computer.
Uses:
Easily track your children computer activities when you are not present at home.
Gives a platform to track fraud activities without your presence.
Easy way to access and delete cookies stored in computer.
Tag :// cool Tricks
Skype 5.5 update contains Facebook Integration Vulnerability.
Now a days,Skype 5.5 is famous due to its direct integration with Facebook.Skype users having account on facebook use some of its functionality.This includes post on wall,comments,status updates or seeing which friend is online on the social networking websites.
Skype integration with facebook allows a serious vulnerability known as session hijacking and various other types of vulnerability founded by David Vieira-Kurz a famous Security-Researcher.
This type of attack uses wall posts which is actually a snippets of code.So,when normal user check its wall post and click on link,their Session has been hijacked.This attack is persistent b/z logging off and on doesn't invalidated the facebook session period.
User's who want this update should wait until skype latest release remove this vulnerability.If you already installed this update,Just remove skype integration from Facebook privacy settings.
David Vieira-Kurz has demonstrated a proof in his video:
http://www.youtube.com/watch?feature=player_embedded&v=IrOyCEdqBOg
Now a days,Skype 5.5 is famous due to its direct integration with Facebook.Skype users having account on facebook use some of its functionality.This includes post on wall,comments,status updates or seeing which friend is online on the social networking websites.
Skype integration with facebook allows a serious vulnerability known as session hijacking and various other types of vulnerability founded by David Vieira-Kurz a famous Security-Researcher.
This type of attack uses wall posts which is actually a snippets of code.So,when normal user check its wall post and click on link,their Session has been hijacked.This attack is persistent b/z logging off and on doesn't invalidated the facebook session period.
User's who want this update should wait until skype latest release remove this vulnerability.If you already installed this update,Just remove skype integration from Facebook privacy settings.
David Vieira-Kurz has demonstrated a proof in his video:
http://www.youtube.com/watch?feature=player_embedded&v=IrOyCEdqBOg
Tag :// cool Tricks,
Tag :// Hacks
Tuesday, April 10, 2012
Ethical Hacking ~ Lab's - 70 Topics Covering almost that Things you need ~ 254.7 MB
!! CERTIFIED ETHCIAL HACKER !!
1: Student Introduction
3: Hacking Laws
4: Footprinting
5: Google Hacking
6: Scanning
7: Enumeration
8: System Hacking
9: Trojans and Backdoors
10: Viruses and Worms
11: Sniffers
12: Social Engineering
13: Phishing
14: Hacking Email Accounts
15: Denial of Service
16: Session Hijacking
17: Hacking Webservers
18: Web Application Vulnerabilities
19: Web based Password Cracking Techniques
20: SQL Injection
21: Hacking Wireless networks
22: Physical Security
23: Linux Hacking
24: Evading IDS Firewall and Honeypot
25: Buffer Overflows
26: Cryptography
27: Penetration Testing
28: Writing Virus Codes
29: Assembly Language Tutorial
30: Exploit Writing 1
31: Exploit Writing 2
32: Exploit Writing 3
33: Reverse Engineering Techniques
34: MAC OS X Hacking
35: Hacking Routers, Cable Modems and Firewalls
36: Hacking Mobile Phones, PDA and Handheld Devices
37: Bluetooth Hacking
38: VoIP Hacking
39: RFID Hacking
40: Spamming
41: Hacking USB Devices
42: Hacking Database Servers
43: Cyber Warfare- Hacking Al-Qaida and Terrorism
44: Internet Content Filtering Techniques
45: Pricy On the Internet
46: Securing Laptop Computers
47: Spying Technologies
48: Corporate Espionage by Insiders
49: Creating Security Policies
50: Software Piracy and W
51: Hacking and Cheating Online Games
52: Hacking RSS and Atom
53: Hacking Web Browsers
54: Proxy Server Technologies
55: Preventing Data Loss
56: Hacking Global Positioning System
57: Computer Forensics and Incident Handling
58: Credit Card Frauds
59: How to Steal Passwords
60: Firewall Technologies
61: Threats and Countermeasures
62: Case Studies
63: Botnets
64: Economic Espionage
65: Patch Management
67: Security Convergence
68: Identifying the Terrorists
69: prova 312-50
70: CEH - Classroom Lab Setup v6
Downloading Links






.jpg)
